ASCWG
ASCWG 2020 Web Challenge G(old)
Cyber WarGames 2020OverviewTogether with my friendMohamed Midowe have been able to solve this challengeChallange Desciption:Difficulty: EasyPoints: 300 pointCategory: WebChallange Link: 10.0.0.5 on LAN Network it is not Available Onlinevulnerability :SSIStepsunderstanding the web appGo to 10.0.0.5you will get this login FormAfter making some routing search on this page like: show source Code, Request, resopsne and Cookies i didn’t find any thing can catche my attention.so,first thing I tried deafault credentials like admin:admin
you will get welcome message with the value of $_POST[‘name’]

i didn’t gey Anything useful
Notice
red rectanglearound file Name and extension.shtmlreturn to Login Form
try Login using anything you will login i will try login with yasser:yasser or xss payload will work but not return with flag or any thing

you will notice that file name was change again
and still with shtml extension
What is shtml ?

open first link and read it

so it may be SSI
Server Side Injection
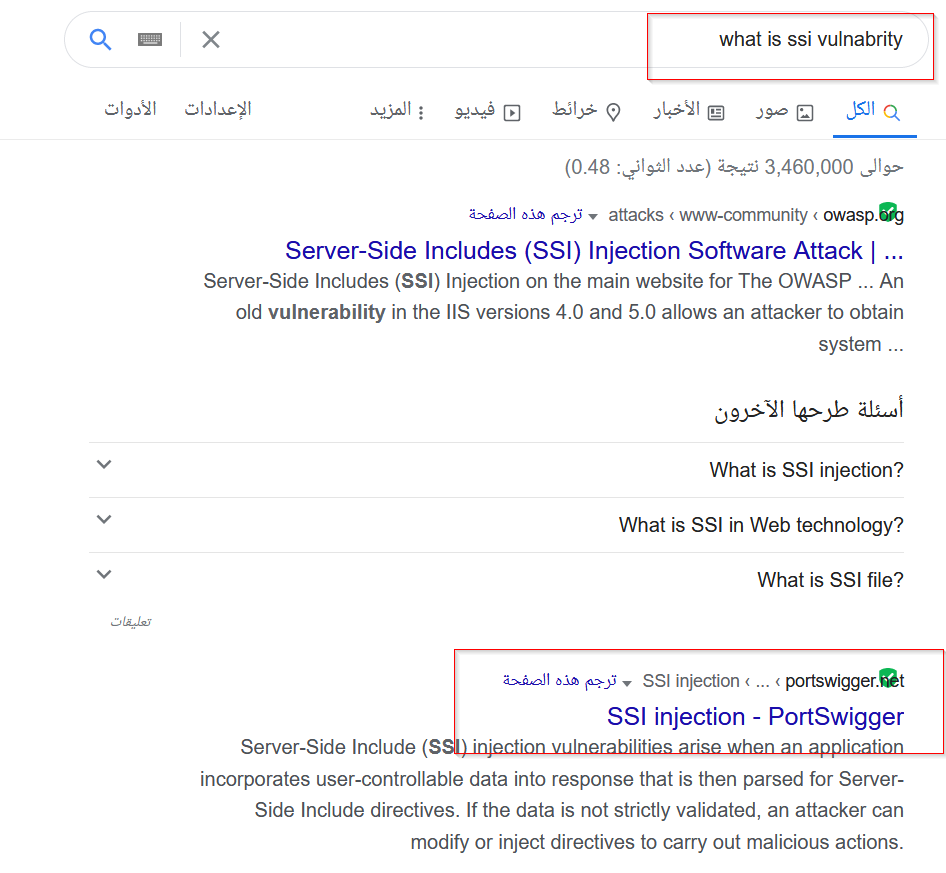
you can using any scanner like burp scanner To be sure
So i will seearch about SSI payloads
Exploit SSI to get the Flag
Fire Burp Suite and injecti payload , What Happend?

Click Follow Redirection

Bing0o0o0o0o we got flag file
let’s try to display this file to get the flag
https://i.ibb.co/Bw3TvB8/redirect-2.png
Click Follow Redirection Again
Bingo0o0o0o we Got The Flag

Quick links
Kourama
Penetesting, Bug Bounty, CTF player.
Last updated