EXternal Xml Entity (XXE)
External XML Entity (XXE)

📚 What Is XXE ?
🤔 Why XXE Happen ?
🧬 XXE Types
⚔ Impact
🔎 How To Find
🛠 Tools
📕 Referance
🔬 Labs
📚 What Is XXE?
What is XML?
XML stands for “Extensible Markup Language”, It is the most common language for storing and transporting data. It is a self-descriptive language. It does not contain any predefined tags like <p>, <img>, etc. All the tags are user-defined depending upon the data it is representing for example. <email></email>, <message></message> etc.
You can know more about XML Entities FROM HERE To avoid wasting time.
Definition of XXE:
An XML External Entity attack is a type of attack against an application that parses XML input and allows XML entities. XML entities can be used to tell the XML parser to fetch specific content on the server.

What is the Document Type Definition (DTD)?
It describes the structure of the document which contains elements and attributes declarations. The element declaration contains the allowable set of elements that will be used within the document. The attribute declaration contains the allowable set of attributes corresponding to each element.
Syntax: -


🤔 Why XXE Happen?
Some applications use the XML format to transmit data between the browser and the server. Applications that do this virtually always use a standard library or platform API to process the XML data on the server. XXE vulnerabilities arise because the XML specification contains various potentially dangerous features, and standard parsers support these features even if they are not normally used by the application.
🧬 XXE Types
Basic XXE
Blind XXE
Blind XXE
Blind XXE vulnerabilities arise where the application is vulnerable to XXE injection but does not return the values of any defined external entities within its responses. This means that direct retrieval of server-side files is not possible, and so blind XXE is generally harder to exploit than regular XXE vulnerabilities.
There are two broad ways in which you can find and exploit blind XXE vulnerabilities:
You can trigger out-of-band network interactions, sometimes exfiltrating sensitive data within the interaction data. You can trigger XML parsing errors in such a way that the error messages contain sensitive data.
⚔ Impact
XML External Entity (XXE) can possess a severe threat to a company or a web developer. XXE has always been in the Top 10 list of OWASP. It is common for lots of websites to use XML in the string and transportation of data and if countermeasures are not taken then this information will be compromised. Various attacks that are possible are:
Server-Side Request Forgery (SSRF)
Remote Code Execution (RCE)
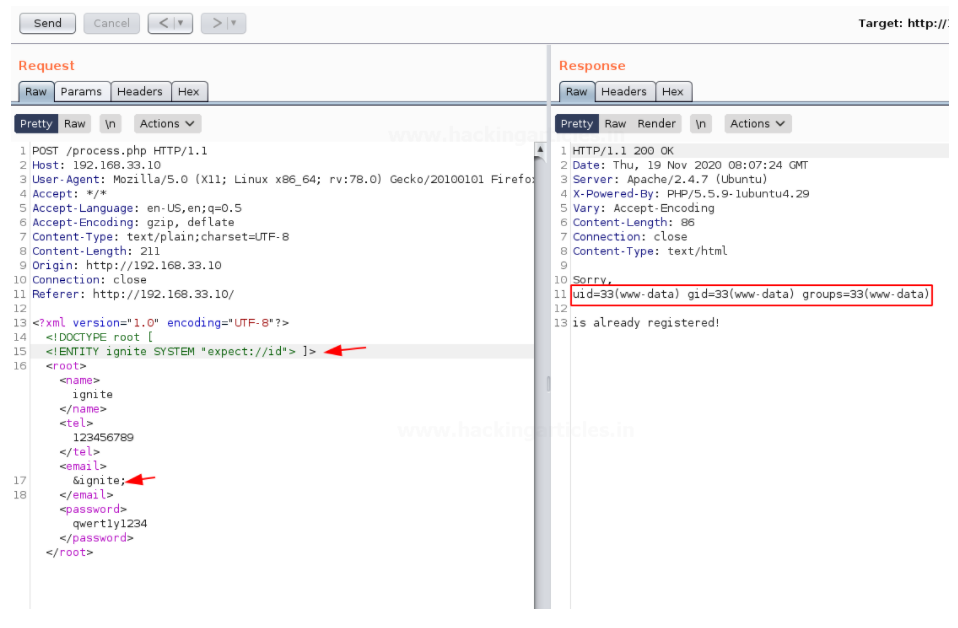
Read Files
Cross-Site Scripting (XSS)
Content-Type: From JSON to XEE To change the request you could use a Burp Extension named Content Type Converter.
Here you can find this example:
File Upload
XXE can be performed using the file upload method. We will be demonstrating this using Port Swigger lab “Exploiting XXE via Image Upload”. The payload that we will be using is:
Understanding the payload: We will make an SVG file as only the upload area accepts only image files. The basic syntax of the SVG file is given above and in that, we have added a text field that will
We will be saving the above code as “payload.svg”. Now on portswigger, we will go on a post and comment and then add the made payload in the avatar field.
🔎 How To Find
Detect any XML data parsing or JSON and try to inject XXE
⚙ Mitigation
The best way to avoid XXE vulnerabilities is to
Altogether disable document type definitions (DTDs) in your XML parser.
If this is impossible, you must disable external entities and document type declarations for your parser.
disable support for
XInclude
🛠 Tools
xxeftp: - A mini webserver with FTP support for XXE payloads
xxexploiter: - Tool to help exploit XXE vulnerabilities
230-OOB: - An Out-of-Band XXE server for retrieving file contents over FTP and payload generation via http://xxe.sh/
XXEinjector: - Tool for automatic exploitation of XXE vulnerability using direct and different out of band methods
oxml_xxe: - A tool for embedding XXE/XML exploits into different filetypes (DOCX/XLSX/PPTX, ODT/ODG/ODP/ODS, SVG, XML, PDF, JPG, GIF)
docem: - Utility to embed XXE and XSS payloads in docx,odt,pptx,etc
otori: - Toolbox intended to allow useful exploitation of XXE vulnerabilities.
📕 Reference
🔬 Labs
Portswigger Portswigger Labs Solution is Here
OWASP Broken Web Applications Project: Install this Machine and will have a lot of Labs like DVWA, BWAPP, Webgoat, etc
Last updated