S3
Simple Storage Service (S3)

📚 What is S3 Bucket
🤔 Why S3 Misconfiguration Happen ?
💥 Exploitation
⚔ Impact
🔎 How To Find
🛠 Tools
⚙ Remediation
📕 Referance
📚 What is S3 Bucket
What is AWS?
AWS stands for Amazon Web Services which is a secure cloud services platform, offering compute power, database storage, content delivery and other functionalities.
What is Amazon S3 ?
Amazon S3 (Simple Storage Service) is one of the popular and widely used storage services. Many companies are using S3 buckets to store their assets such as user profile pictures, static resources, and anything as per their business logic and needs.
Files can be served either privately (via signed URLs) or publicly via an appropriately configured ACL (Access Control List) or ACP (Access Control Policy).
Like:
🤔 Why S3 Misconfiguration Happen ?
S3 Attacks
We will go through the specifics of each level and identify the dangerous cases where weak ACLs can create vulnerable configurations impacting the owner of the S3-bucket and/or through third party assets used by a lot of companies.
However, if the buckets are not configured properly, or are unclaimed, an attacker can probably perform some mischievous actions such as
S3 Bucket Takeover
S3 Content Takeover
💥 Exploitation
Requirements
To test for the access controls of the S3 Bucket, the best way is to use, AWS CLI and default commands.
Install AWS CLI.
Check whether it is perfectly installed or not.
Then you can make aws account and Provide AWS ACCESS Key & Secret to configure AWS CLI. You can watch this video Steps.
Add Provide AWS ACCESS Key & Secret to configure AWS CLI.
Basic tests
Checking for S3 Open Buckets & Finding bucket name
Using AWS CLI to Check S3 Bucket Access Controls
Increasing Impact by looking at all C.R.U.D (Create, Read, Update & Delete) actions.
Listing files
Move a file into the bucket
Download every thing
Delete Files
Subdomain takeover - S3 bucket
S3 buckets are spawned out of storage requirements and are bound to a particular domain. Sometimes these buckets are not deleted after they have served their purpose which may escalate to a complete takeover of a subdomain of the host. Consider the following example:
An S3 bucket may be created and its URL (http://storage.example.com.s3-website.ap-south-1.amazonaws.com) may be bound to a subdomain(Eg: “https://storage.example.net”.) belonging to the organization to obfuscate the AWS S3 URL. This is done by adding an alternate domain name(CNAME).
Later when this bucket is deleted from AWS S3, but the CNAMEs record in the Route53 is not removed, an attacker may create an AWS S3 bucket with the same name and the malicious contents of this bucket will be served on the victim’s domain(eg: storage.example.net), Hence taking over the subdomain.
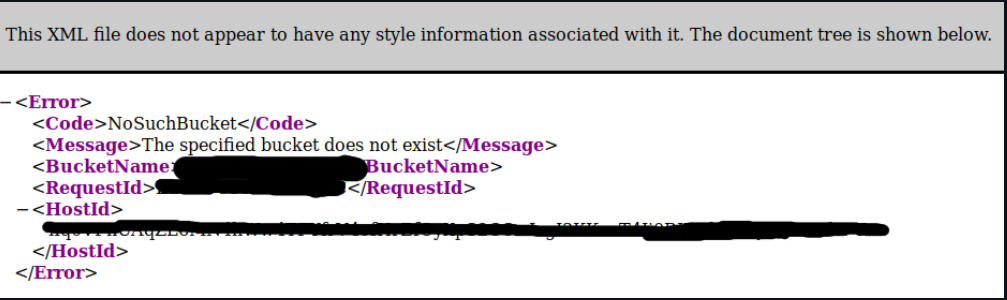
Identifying this Vulnerability The first step in identifying this vulnerability is looking for an error page that has the message “404 Not Found” and the message “NosuchBucket”.
Or from EdOverflow
AWS/S3
Vulnerable
The specified bucket does not exist
⚔ Impact
Possible vulnerabilities:
Reflected XSS.
Stored XSS / asset control. HTML-file.
Denial of server.
Information Disclosure. If we can list objects we might find sensitive information.
RCE. If the bucket contains modifiable executables this can result in Remote Code Execution (RCE) depending on where the executables are being used and if/by whom they are being downloaded.
🔎 How To Find
FFUF
You can put this in your recon after get subdomains steps or just using one of Tools Below
Follow Twitter #BugBountyTips hashtag to get new tricks to find an s3 bucket during your Recon or by using Automated Tools like:
Lazy S3,S3Scanner,S3 Bucket Finder & Mass3
🛠 Tools
Lazy S3: A Ruby script to brute force for AWS s3 buckets using different permutations.
Mass3:Quickly enumerate through a pre-compiled list of AWS S3 buckets using DNS instead of HTTP with a list of DNS resolvers and multi-threading.
S3 Bucket Finder: PHP tool to brute force Amazon S3 bucket ز
S3Scanner: A tool to find open S3 buckets and dump their contentsز
⚙ Remediation
Make sure all the Amazon S3 buckets you are using are marked as private.
📕 Referance
PayloadsAllTheThings janijay007 detectify pravinponnusamy Harsh Bothra EdOverflow
Last updated