🛜Wireless Networks Penetration Testing
The main components of a wireless network

Clients/Stations: These devices connect to the wireless network provided by the access point. Clients or stations can include any Wi-Fi-enabled device, such as laptops, smartphones, tablets, printers, and more. Each client or station communicates with the access point to send and receive data over the wireless network. هي الأجهزة المتصلة على الشبكة سواء موبايل لابتوب تابلت وهكذا
Access Point (AP): This device creates a wireless local area network (WLAN) by connecting to a wired router, switch, or hub via an Ethernet cable. The AP then broadcasts a Wi-Fi signal that allows Wi-Fi-enabled devices, such as laptops, smartphones, tablets, and IoT devices, to connect to the network wirelessly. الجهاز المسؤل عن عمل شبكة الوايرليس في المكان عن طريق اتصاله بالرواتر عن طريق محموعه من الأسلاك للإتصال عن طريق ال Clients
Wireless Access Points Modes
Wireless APs can operate in multiple modes. Each mode is designed for a particular scenario, impacting how devices connect and communicate within a network. Let's explore these modes:
APs Modes:

01 locall Mode
It is also called Access Point Mode. This is the default setting for indoor access points and all APs support it. In local mode, the access point handles the reception and transmission of data packets between the wired network and wireless clients. This mode is the most common mode of operation for wireless access points because it achieves optimal performance by offloading client traffic directly onto the wired network, thus maintaining high throughput and reducing wireless congestion.

02 Client Mode
In this mode, the AP connects to another wireless network as a client device, enabling devices wired to the AP (like a desktop computer without a Wi-Fi card) to access the wireless network. It's essentially the reverse of the common use of an access point, bridging a non-wireless device to a wireless network rather than the other way around. It's beneficial for providing network connectivity to legacy devices that lack Wi-Fi capability.

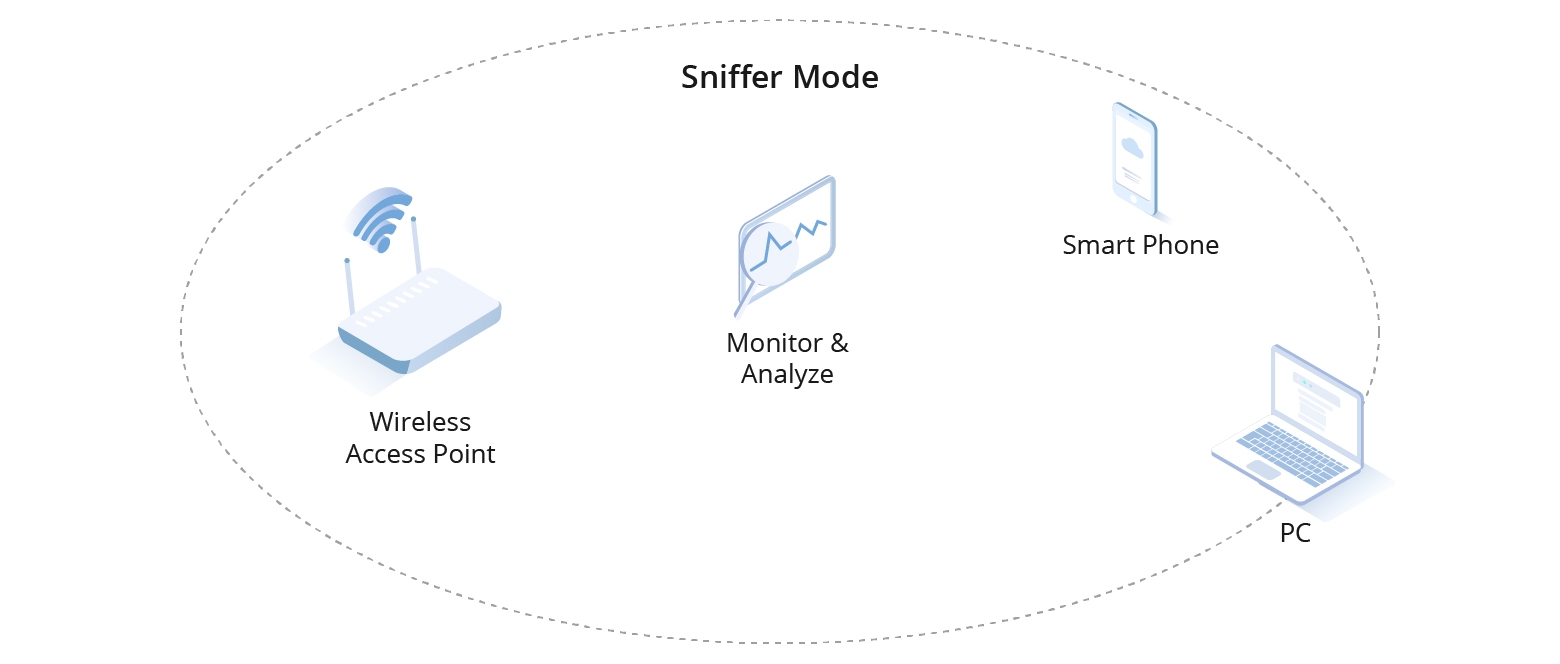
03 Monitor Mode
It is a diagnostic setting that captures all nearby wireless traffic, regardless of its destination. It's used for troubleshooting, security analysis, and monitoring network performance. Devices in sniffer mode do not engage in network communication but passively listen to the wireless spectrum, gathering data for further study with specialized software. It's a tool for administrators to analyze and understand network traffic patterns and potential issues.
BSS, ESS, BSSID, SSID
SSID (Service Set Identifier): An SSID is the name of a Wi-Fi network. It's what you see when you scan for available Wi-Fi networks on your device. It's used to identify and differentiate between different wireless networks.

BSSID (Basic Service Set Identifier): A BSSID is a unique identifier attached to each wireless access point. It's a MAC address assigned to the radio in the access point hardware. BSSID helps in uniquely identifying each access point in a wireless network.

BSS (Basic Service Set): A BSS is a set of all stations (wireless devices) that can communicate with each other in a wireless network. It's essentially a single access point and all the devices connected to it.

ESS (Extended Service Set): An ESS is a collection of interconnected BSSs (Basic Service Sets) and integrated LANs (Local Area Networks) that appear as a single BSS to the logical link control layer at any station associated with one of those BSSs. It's a group of interconnected BSSs that form a larger wireless network, typically managed by the same administrative entity (like a single Wi-Fi network spanning multiple access points in a large building or campus).

Example:

Wi-Fi Security Standards

WEP (Wired Equivalent Privacy): WEP was one of the earliest encryption protocols to secure wireless networks. It aimed to provide a level of security equivalent to that of a wired network. However, WEP is now considered weak and easily crackable due to its use of a static encryption key and vulnerabilities in its implementation.
802.11x: This term refers to a family of standards for wireless local area networks (WLANs) developed by the Institute of Electrical and Electronics Engineers (IEEE). The "x" in 802.11x can be replaced with different letters or numbers to indicate specific variations of the standard. For example, 802.11b, 802.11a, 802.11g, 802.11n, 802.11ac, and 802.11ax are different versions of the 802.11 standard, each offering different features, speeds, and frequency bands.
WPA2 (Wi-Fi Protected Access 2): WPA2 is a security protocol designed to secure wireless computer networks. It replaced WPA (Wi-Fi Protected Access) and improved upon the security features of WEP. WPA2 uses the Advanced Encryption Standard (AES) encryption algorithm and provides stronger security mechanisms than WEP or the original WPA. However, vulnerabilities have been discovered in WPA2, leading to the development of WPA3.
WPA3 (Wi-Fi Protected Access 3): WPA3 is the latest security protocol for Wi-Fi networks. It introduces several security enhancements over WPA2, including stronger encryption, protection against offline dictionary attacks, and improved security for IoT devices. WPA3 aims to address the weaknesses and vulnerabilities found in previous Wi-Fi security protocols, providing higher security for wireless networks.
WPA vs WPA2

802.11_Wi-Fi Connection

WI-FI Network Discovery:
هنا الأكسيسز بوينت بيبدأ يبعت إشارات يعلن عن وجوده عشان أي كلاينت يقدر يشوفه ويتصل بيه من خلال المرحلة الي بعدها وهي مرحلة المصادقه
Authentication:
المرحلة دي بيتم فيها عملية التأكيد والتشفير بإستخدم اليوزر والباسورد أو على حسب ال Configuration المستخدم
Association:
بعد ما خلصنا المرحلتين السابقين محتاج نبعت ريكوست كمان عشان يقدر يدخلنا او يربطنا على الواي فاي نتورك دي
Four-Way Handshake, key hierarchy
In detail you can read this Blog: https://www.wifi-professionals.com/2019/01/4-way-handshake
AP Send Anonce (random number) to the client to generate PTK (1)
Client Send PTK + Snonce (random number) + MIC (Message Integrity Check) to make sure when the access point can verify whether this message is corrupted or modified for the AP to generate PTK (2)
and Compare Both PTK Values
AP sends a message to the client device containing GTK (Group Temporary Key) + MIC (Message Integrity Check)
The message ACK will be sent from the client to AP just to confirm that the Keys have been installed.

PTK (Pairwise Transient Key):
A pairwise Transient key is used to encrypt all unicast traffic between a client station and the access point. PTK is unique between a client station and an access point. To generate PTK, the client device and access point need the following information.
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
Anonce is a random number generated by an access point (authenticator), and Snonce is a random number generated by the client device (supplicant). MAC addresses of supplicant (client device) and MAC address of authenticator (access point). PRF is a pseudo-random function which is applied to all the input.
PTK is dependent on another high-level key PMK (pairwise master key) which is discussed below.
GTK (Group Temporal Key):
A group temporal key is used to encrypt all broadcast and multicast traffic between an access point and multiple client devices. GTK is the key that is shared between all client devices associated with 1 access point. For every access point, there will be a different GTK which will be shared between its associated devices.

The SSID + PassPharse will be used to Generate PSK/PMK and merged with ANONCE AND SNONCE to Generate PTK.

Types of Wi-Fi access points

Last updated